This blog post will explore the changing landscape of ransomware attacks in terms of what phishing emails look like, how ransomware attackers are using social engineering tactics to convince users to pay the ransom, and how businesses can prepare for these sorts of attacks by training staff to spot ransomware while creating prevention/response frameworks.
How Ransomware Attacks Used to Function
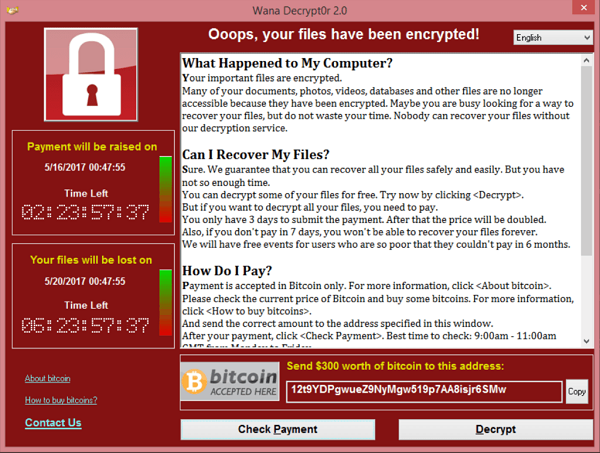
The WannaCry ransomware attack is estimated to have infected over 200,000 systems across the globe in 2017. Despite this, WannaCry was a financial flop only netting just under $400,000 in ransom payments. (Webtitan)
The reason WannaCry wasn’t a successful ransomware attack is because a WannaCry attack only encrypted the active system, not the backups. Nor did the team that distributed WannaCry try to extort the organizations it infected by threatening to release data unless the ransom payment was made. As a result, businesses simply restored backups to remove the ransomware.
WannaCry is a perfect example of how a typical ransomware attack would play out just a couple of years ago – and it led to organizations responding by simply deploying backups.
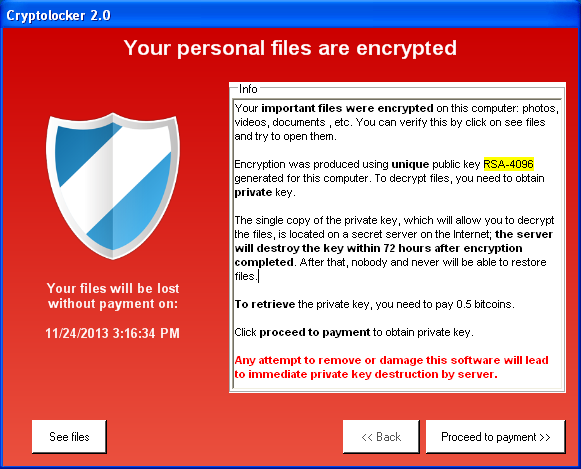
The attack sequence goes like this: Ransomware finds its way into an organization’s system (likely through a phishing email). Then, an employee somehow activates the malicious code which quickly encrypts all the files on a system. The ransomware then provides a prompt telling the user that their system is locked and the user must pay a ransom using crypto currency. Here is an example prompt using the ransomware CryptoLocker:
Ransomware is Becoming More Sophisticated – Here’s Why
Because businesses have learned from previous high-profile attacks, like the infamous WannaCry attack, how to protect themselves against ransomware, it has forced groups, like DarkSide (which has lately become a household name in cybersecurity), to change how ransomware is deployed, and what is offered in exchange for the ransom.
Ransomware syndicates studied the low success rate of mass attack campaigns like WannaCry and realized that if they only target the current system state, and only request payment in exchange for access, most businesses will simply resort to backups rather than pay a ransom.
Couple that with both organizations and individuals being able to more intelligently spot ransomware, cybercriminal syndicates have come to see the value in choosing a coordinated attack utilizing users’ personal information. Criminals may also give themselves admin permissions and or threaten to leak data in hopes an organization pays to avoid extortion.
Covid-19 and ransomware as a service (RaaS) have also led to a dramatic increase in ransomware attacks in recent months.
Let’s do an in-depth dive into all these factors that have led to an increase in the number of ransomware attacks.
COVID-19
 COVID-19 has been a massive gift to cybercriminals. Because employees are working from home, many of them have switched to using personal devices and accessing organization apps from their home network. This creates attack surfaces that aren’t monitored by IT and do not have proper monitoring and anti-virus.
COVID-19 has been a massive gift to cybercriminals. Because employees are working from home, many of them have switched to using personal devices and accessing organization apps from their home network. This creates attack surfaces that aren’t monitored by IT and do not have proper monitoring and anti-virus.
A Generation Born with Internet

It is much harder for cybercriminals to target younger, more web-savvy users because they grew up with the internet (and all its many scams). Growing up with the internet has allowed many younger members of the workforce to more easily identify emails with malicious URLs, poor grammar, or those impersonating co-workers.
As a result, the low-hanging fruit has often become older generation users that often can’t as easily identify malicious emails.
Cybercriminals are adapting to more aware younger users by utilizing stolen personal information, engaging in email conversations, and developing convincing deep fake personas.
Backups

Businesses and users have become much better at implementing backups. Traditionally, backups were all a business needed to thwart virtually any ransomware attack. All the business had to do is simply restore their system to a previous state and the ransomware was gone.
However, ransomware has responded by waiting longer between the infection and encryption stages as well as making sure to target backups within the network as well.
Cybercriminals have also realized it can become far more lucrative to extort data rather than trap it. For example, threatening to release proprietary code if a business is unwilling to pay the ransom.
How ransomware is Adapting

(Image: In 2021 CNA Insurance allegegly paid a $40,000,000 ransom – the highest on record)
The previous section gave a short overview of cybercriminal’s response to the increasingly hostile situation for launching a successful ransomware attack. In this section, I will detail how ransomware has adapted and what organizations and individuals need to look out for.
COVID-19
COVID-19 was a blessing for ransomware syndicates because it dramatically expanded potential attack vectors. many organizations no longer have as much direct oversite over employees, have increasingly embraced bring your own device (BYOD) to get employees remote faster, and allow employees to access critical data and apps outside the organization’s internal network, ransomware can spread much easier.
Take this scenario: Barbara works for an insurance company. She accesses her email via her unsecured home network and connects to the corporate VPN to access the employee-only application to process claims. She accesses the application on her company-provided laptop but it is not monitored by IT and she uses it for personal use often.
The above scenario is a security nightmare. There is a likelihood barbara will receive targeted malicious emails due to her occupation. With IT not being able to keep a close eye, and potentially unavailable to answer questions, Barbara might accidentally respond and start a conversation with a spoofed or otherwise misrepresentation email from a cyber-criminal (perhaps pretending to work in IT). If the criminals get her to download something malicious, they could use Barbara to unknowingly open a tunnel between the servers and barbara, and infecting devices within the network.
Deep Faking

Employees and organizations have become much better at spotting malicious emails and sites. As a result, cybercriminals have turned to deep faking to connect with users by using elaborate personas that can sometimes take months to pull off.
A perfect story of this was the story of a UK energy company that was tricked into wiring $220,000 to a Hungarian company due to an A.I. that could fake a call as the CEO. Thieves are now using AI deepfakes to trick companies into sending them money – The Verge
Deep faking in the cybersecurity context can be a phone call, text, email, or another medium that uses A.I. or extremely engaging social engineering.
A criminal could call someone in accounting after performing deep research on the CEO of that company. That criminal could sound nearly identical to the CEO on the phone, then tell the accountant they will send an email summarizing their conversation. The criminal can then send an email from a spoof of the CEO’s email. The timeliness of these events could trick anyone.
Spear-Phishing

Cybercriminals are realizing that sending broad email attacks that target hundreds of thousands of users is not effective anymore. By nature, broad emails are not personalized and are less easy to nurture into becoming more sophisticated attacks with real dialogue. Phishing emails have historically had a reputation for being cookie-cutter with poor grammar (we’ve all heard of the Nigerian prince email campaign).
Now, with the breadth of user data available for purchase and the amount of personal data users voluntarily publish on sites like Facebook or LinkedIn, cybercriminals are finding tremendous value in spear phishing.
Spear-phishing is the practice of targeting a select few individuals rather than the masses. A spear-phishing campaign can be conducted much like a sales or marketing campaign where the criminals will target certain industries, titles, or demographics.
Example: a cybercriminals syndicate designs ransomware and targets the insurance industry. They will then find employees with potential access access to the network within the company they want to target. They will then conduct research using purchased data, social media, account hacks, etc to spy and make sure they send the right message to the right person. After successfully engaging with someone at a targeted company for a while, incorporating back and forth conversation, the criminals can get that employee to click a malicious link or file, which can then spread the ransomware.
When spear phishing, those that are “low hanging fruit” are often the target. These are those that might have difficulty discerning fake emails. Examples include remote workers, older workers, and those that have minimal exposure to leadership email language.
Case Study
An example of just how convincing a spear-phishing campaign can be is the example of a journalist from India by the name of Nidhi Razdan that thought she was Given a position at Harvard. The campaign targeted her because they found she spoke at a Harvard event in the past by invitation from Harvard. The hackers and journalists corresponded for a long time, even going as far to perform an interview, establish employment terms, and provide a teaching schedule. She only found out it was a scam after she contacted Harvard and they informed her she was never offered the position and the Harvard human resources email she was corresponding with did not exist.
The author has written about her experience and you should read it to learn just how sophisticated phishing campaigns can be.
I Am Nidhi Razdan, Not A Harvard Professor, But… (ndtv.com)
Becoming Extortive

Cybercriminals have changed the purpose of ransomware entirely in some cases. Rather than blocking an organization from its data, the criminals instead extort the organization such as by increasing privileges giving themselves massive control over the business, threatening to release intellectual properties or assets like code. In this way, a business cannot just simply rely on backups. The threat of a data leak compels many to pay the ransom. Especially if they are in an industry that has strict consequences for data leaks like insurance or healthcare.
Extortion dramatically changes how companies implement ransomware protection. Instead of reactive solutions like anti ransomware software or preparing robust backups, your organization must now put prevention at the forefront. In an industry like healthcare, where the data itself is incredibly valuable to extort, an attack cannot breach the prevention systems in place or your company may already have lost. The main concern becomes a data leak rather than if you pay the ransom.
Ransomware as a Service (RaaS)

Ransomware as a service allows cybercriminals to join an established and growing market of ransomware for purchase. The use of this service makes it easier than ever before for criminals with little or no coding knowledge to launch crypto-malware campaigns because they only need the technical skills required to operate web hosting services and distribute spam emails.
There are two notable dangers ransomware as a service creates:
The first is that because ransomware is now available to the masses, criminals with little coding knowledge can now engage in the lucrative market for ransomware attacks. This dramatically increases the chance a business will be attacked. These lesser criminals also may not have the knowledge on how to restore data properly if a ransom is paid. And they are likely performing infrequent or one-off attacks so they don’t have a reputation to protect like established cybercriminal syndicates.
The second danger is that ransomware criminals can now form a community and learn from each other. This allows criminals to become smarter and adapt much faster. And with a greater number of ransomware products on the market, the progress towards more powerful and efficient ransomware becomes far quicker.
How to Respond
Ransomware has changed and so has the playbook for preparing for and responding to a ransomware attack. While much of the same precautions stay unchanged, new solutions have come to market to help organizations better prepare for and respond to attacks.
Understand Your Industry’s Risk to a Ransomware Attack
Certain industries are at a far greater risk of being on the receiving end of a ransomware attack than others. Health data for example has long been prized by criminals because businesses that guard Health data are at risk of severe legal and financial penalties should that data become encrypted, or worse, leaked.
Here are the industries that are the most at risk of a ransomware attack:
- Healthcare
- Legal/Law
- Energy
- Utility
- Education
- Finance
- Government
If your business falls into any of these categories, it is at immediate risk. You should seek immediate ransomware protection and may want to get in touch with a professional cybersecurity auditing firm that can analyze your vulnerabilities.
If your business is not in the above categories, you are still increasingly at risk of being hit with a ransomware attack. You may also be more tempted to pay the ransom if attacked because the ransom may be lower and your business may not suffer the same legal ramifications. Your business should implement most if not all the steps below to minimize your risk of a ransomware attack.
Establish a Response Framework
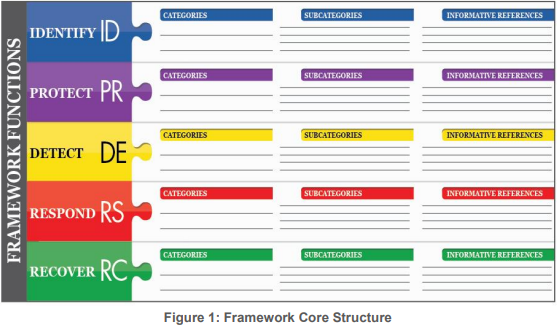
The NIST framework is a helpful model for organizations to use when establishing their ransomware response plan. NIST has broken down the four steps of handling an incident into specific functions that can be assigned to team members within your organization, ensuring all roles are covered in the event something happens and resources need to be enacted. This ensures that everyone knows what they should do if or when an attack occurs. Involve Key Stakeholders
Here is how the framework works, NIST has defined four primary functions:
- Identify: a business identifies its most important functions, assets, people systems, and capabilities of the organization and establishes tiers of importance so that they know which vulnerabilities to tackle first. This allows a business to focus and become more efficient at covering attack vectors. categories can include things like risk assessment, asset governance, risk management strategy, etc.
- Protect: Create a list of the ways you can protect critical systems from a breach. Categories can include things like training, access control, information protection procedures, etc.
- Detect: create a set of steps to detect if a cybersecurity event occurred. This allows your organization to diagnose whether there is a breach that needs immediate attention. categories can include detection process, anomalies, security monitoring, etc.
- Respond: Develop actions taken in response to an attack. These will help with containing and stopping ransomware. Categories include communication, response planning, mitigation, improvements, etc.
- Recover: Outlines what needs to be done to facilitate a timely recovery and resume normal operations. Categories include recovery steps, communication, systems improvements, etc.
NIST consists of categories and sub-categories:
- Categories: the broad description of what needs to happen. For example, communication. This is an umbrella for more specific communication actions that need to take place.
- Sub-categories: these are the more specific actionable outcomes. For example, in the category “identity management”, you might have a sub-category like. “All employees will use 2FA when logging into organization accounts”.
You can view the specifics of the NIST framework here – the official document covers the framework more in depth. But even just using the basic one sheet framework can help your organization spot an exploit and develop proper planning and response actions. You can also use different or even self-developed frameworks should you feel that there is another that better suits your organization’s needs.
Backups
Modern sophisticated ransomware now targets backup, so the old strategy of using backups to counter an attack may not work. Backups are still important, however. But the backups your organization keeps must be less penetrable. There are 3 tiers of backups your organization should consider.
The first tier is readily available standard backups. These are important because beyond ransomware your organization will likely need to revert changes, so it’s important you have backups that can be modified and easily applied over running systems. These backups include snapshots from your hypervisor or services like Veeam.
The second tier is immutable backups. these are backups that are immutable, or unmodifiable. This means they can be restored to a system but not modified in place on the live OS. These backups should include images of your OS and application installations for short-term recovery point objectives (RPOs). Immutable backups can either be online or offline, with offline offering greater security should you get a network infection.
Why not just keep immutable backups? Because they cannot be modified AT ALL! This means that should your organizations need to make any changes they cannot. So these backups are best kept in case of emergency.
The third tier is air-gap backups. air-gap backup is a backup of a live system that is not connected to any network (or the cloud). An example of an air-gap backup would be tapes physically stored on-premises. They are completely inaccessible from the network or system and therefore unhackable.
Air-gap is important for businesses that deal with sensitive user data where should that data become compromised, there are consequences. Businesses like healthcare for example must also keep data for several years by law. Air-gap offline backups allow healthcare companies to store vast quantities of data securely and cost-effectively.
Implement Regular Training

Regular training is a must these days. Regular training goes a long way because most ransomware attacks occur due to phishing emails, social engineering, RDP exploits, and leaked credentials. Training staff to take care of their credentials, understand good security practices, and treat digital interaction with skepticism will go a long way towards developing your business’ ransomware protection.
Here’s how training could play out at an SMB. When a new staff member is onboarded they receive relatively comprehensive training from IT on what is expected from them regarding security. These can include regular password changes, enabling 2FA, and how to spot malicious emails. IT can then help the employee get set up with an authenticator app, let the employee know password requirements, provide info on device acceptable use. If there is a particular vulnerability that the employee must be made aware of, this can be done during orientation.
Once the employee has had time to settle in their role, they will join the other staff for quarterly training led by IT or other parties that can help with security training. Staff will work in groups and try to identify malicious emails or other forms of communication. For example, letting them listen to a deep fake call and providing the employees a proper response when in doubt.
Employees can then, on their own time once a quarter reset passwords so that systems are harder to hack. The system can be automated to alert employees of password changes and automatically disabling their current password after a certain date.
Establish Policies
Taking guidelines like “urging to change passwords once a quarter” and turning them into requirements like “required to change password once a quarter” can help thwart ransomware. Humans are naturally sloppy when it comes to security because life presents other, immediately visible challenges. However, that doesn’t excuse an organization from not implementing them. Instead, it’s best to have IT or a manager establish policies regarding security. Here are some common ones that can help organizations prevent ransomware.
- requiring frequent password changes
- requiring 2FA to access organization applications
- outlining acceptable use for devices that access organization apps and systems
- recording login/logout
- not using company email to sign up for non-work sites
Implement Zero Trust

One of the most effective forms of ransomware protection is to implement Zero Trust within your organization. Zero Trust is a framework that combines multiple advanced identity management programs to constantly validate users whether inside or outside the organization. For example, your business’ zero-trust policy may require users whether inside or outside the organization to access all apps using a VPN, log in with 2FA, and be a part of an active directory that bestows complete control over user accounts to a high-level systems admin within the organization.
Businesses are increasingly implementing zero trust as one of many forms of ransomware protection.
Zero trust can be difficult to implement for SMBs however because it requires one or a team of competent systems administrators who have the time to actively manage all devices accessing programs and the network. However, if your business can implement zero-trust internally or get help from a third party like an MSP, zero-trust remains an important part of a strong ransomware protection plan.
Invest in Cybersecurity
Virtually all large businesses have a sizable investment in cybersecurity services, systems, and software. And more SMBs are starting to invest a portion of their IT expense directly into cybersecurity.
Cybersecurity is broad and can cover all kinds of services. These commonly include, but are not limited to:
- professional security auditing services
- anti-virus software (Norton, McAffee, Kaspersky, etc)
- ransomware-specific software (Zebra Ransomware Stopper)
- Software/hardware firewalls
- Malware tools (Malware bytes, Bitdefender)
Cyber Insurance
Cyber insurance is not cybersecurity because it plays no role in prevention or recovery, but it provides payment should a business become infected with ransomware. The payment foremost covers liabilities related to ransomware, but can also provide payments to recover data or continue business operations depending on the policy.
Here is an example of a policy from nationwide as an example of what a major insurance company will offer.
Cyber insurance is a newer offering and quickly becoming more expensive as insurance companies see a dramatically increasing number of claims. Most SMBs do not have cyber insurance but it is common now for larger companies that can afford the extra policy.
Consider Linux
Lately, the Windows operating system from Microsoft has been falling out of favor for organizations. Linux in comparison is growing because it is free and open-source (FOSS) and generally doesn’t have the same breadth of vulnerabilities for ransomware and malware to abuse.
Unless your organization runs an application that requires Windows, it should absolutely consider a Linux operating system for running its server or cloud infrastructure. There are many distributions of the Linux operating system to choose from. Common distros prized for stability and security are Debian (used by NASA), CentOS, RedHat Enterprise Linux, and Manjaro.
If employees use a cloud desktop experience (using services like Microsoft 365 or Google Drive) to power their day-to-day operations. A Linux desktop operating system may help tackle security vulnerabilities. However, using Linux is less viable for most organizations than a server setup because the Linux operating system has less support for mainstream applications like Microsoft Office.
Anti-Ransomware Software

If you search for “ransomware protection” or “anti ransomware software” you will likely be bombarded with many competing antivirus programs. A true anti ransomware program solution will not be part of a broader proprietary cybersecurity suite, but will instead seamlessly integrate with your existing solutions.
Zebra Ransomware Stopper is an example of an anti-ransomware software. It is a standalone program, not part of a greater cybersecurity suite, that is focused on rooting out ransomware that has already infected your system. It uses deception technology that deploys honeypot files to attract and trap ransomware, stopping the encryption process from further infecting your machine and network.
Many businesses are actively looking for anti-ransomware software so that they have a plan B in case their preventative measures fail and a system does become infected. If you are a reseller or business looking for a last line of defense consider reaching out to us so we can teach you more about this amazing solution.
You can contact us here to learn more.
Summary
Ransomware is evolving, and because of that, your strategy for preparing and recovering from ransomware needs to change too. Ransomware attacks are increasing in frequency, becoming more sophisticated, turning towards extortion, and using personal information against targets.
The best thing your business can do is to develop a bulletproof strategy that your organization can follow consistently long term. Start with developing a framework then identify services and policies that can help turn that framework into a realistic actionable plan.
To learn more about Zebra Ransomware Stopper and how it can potentially save your business from the long-term consequences of a ransomware attack, you can view our page here.
Ransomware is evolving. Not just because cybercriminals are learning from past mistakes, but because businesses and individuals are getting smarter about detecting and responding to ransomware.
This blog post will explore the changing landscape of ransomware attacks in terms of what phishing emails look like, how ransomware attackers are using social engineering tactics to convince users to pay the ransom, and how businesses can prepare for these sorts of attacks by training staff to spot ransomware while creating prevention/response frameworks.
How Ransomware Attacks Used to Function

The WannaCry ransomware attack is estimated to have infected over 200,000 systems across the globe in 2017. Despite this, WannaCry was a financial flop only netting just under $400,000 in ransom payments. (Webtitan)
The reason WannaCry wasn’t a successful ransomware attack is because a WannaCry attack only encrypted the active system, not the backups. Nor did the team that distributed WannaCry try to extort the organizations it infected by threatening to release data unless the ransom payment was made. As a result, businesses simply restored backups to remove the ransomware.
WannaCry is a perfect example of how a typical ransomware attack would play out just a couple of years ago – and it led to organizations responding by simply deploying backups.
The attack sequence goes like this: Ransomware finds its way into an organization’s system (likely through a phishing email). Then, an employee somehow activates the malicious code which quickly encrypts all the files on a system. The ransomware then provides a prompt telling the user that their system is locked and the user must pay a ransom using crypto currency. Here is an example prompt using the ransomware CryptoLocker:

Ransomware is Becoming More Sophisticated – Here’s Why
Because businesses have learned from previous high-profile attacks, like the infamous WannaCry attack, how to protect themselves against ransomware, it has forced groups, like DarkSide (which has lately become a household name in cybersecurity), to change how ransomware is deployed, and what is offered in exchange for the ransom.
Ransomware syndicates studied the low success rate of mass attack campaigns like WannaCry and realized that if they only target the current system state, and only request payment in exchange for access, most businesses will simply resort to backups rather than pay a ransom.
Couple that with both organizations and individuals being able to more intelligently spot ransomware, cybercriminal syndicates have come to see the value in choosing a coordinated attack utilizing users’ personal information. Criminals may also give themselves admin permissions and or threaten to leak data in hopes an organization pays to avoid extortion.
Covid-19 and ransomware as a service (RaaS) have also led to a dramatic increase in ransomware attacks in recent months.
Let’s do an in-depth dive into all these factors that have led to an increase in the number of ransomware attacks.
COVID-19
 COVID-19 has been a massive gift to cybercriminals. Because employees are working from home, many of them have switched to using personal devices and accessing organization apps from their home network. This creates attack surfaces that aren’t monitored by IT and do not have proper monitoring and anti-virus.
COVID-19 has been a massive gift to cybercriminals. Because employees are working from home, many of them have switched to using personal devices and accessing organization apps from their home network. This creates attack surfaces that aren’t monitored by IT and do not have proper monitoring and anti-virus.
A Generation Born with Internet

It is much harder for cybercriminals to target younger, more web-savvy users because they grew up with the internet (and all its many scams). Growing up with the internet has allowed many younger members of the workforce to more easily identify emails with malicious URLs, poor grammar, or those impersonating co-workers.
As a result, the low-hanging fruit has often become older generation users that often can’t as easily identify malicious emails.
Cybercriminals are adapting to more aware younger users by utilizing stolen personal information, engaging in email conversations, and developing convincing deep fake personas.
Backups

Businesses and users have become much better at implementing backups. Traditionally, backups were all a business needed to thwart virtually any ransomware attack. All the business had to do is simply restore their system to a previous state and the ransomware was gone.
However, ransomware has responded by waiting longer between the infection and encryption stages as well as making sure to target backups within the network as well.
Cybercriminals have also realized it can become far more lucrative to extort data rather than trap it. For example, threatening to release proprietary code if a business is unwilling to pay the ransom.
How ransomware is Adapting

(Image: In 2021 CNA Insurance allegegly paid a $40,000,000 ransom – the highest on record)
The previous section gave a short overview of cybercriminal’s response to the increasingly hostile situation for launching a successful ransomware attack. In this section, I will detail how ransomware has adapted and what organizations and individuals need to look out for.
COVID-19
COVID-19 was a blessing for ransomware syndicates because it dramatically expanded potential attack vectors. many organizations no longer have as much direct oversite over employees, have increasingly embraced bring your own device (BYOD) to get employees remote faster, and allow employees to access critical data and apps outside the organization’s internal network, ransomware can spread much easier.
Take this scenario: Barbara works for an insurance company. She accesses her email via her unsecured home network and connects to the corporate VPN to access the employee-only application to process claims. She accesses the application on her company-provided laptop but it is not monitored by IT and she uses it for personal use often.
The above scenario is a security nightmare. There is a likelihood barbara will receive targeted malicious emails due to her occupation. With IT not being able to keep a close eye, and potentially unavailable to answer questions, Barbara might accidentally respond and start a conversation with a spoofed or otherwise misrepresentation email from a cyber-criminal (perhaps pretending to work in IT). If the criminals get her to download something malicious, they could use Barbara to unknowingly open a tunnel between the servers and barbara, and infecting devices within the network.
Deep Faking

Employees and organizations have become much better at spotting malicious emails and sites. As a result, cybercriminals have turned to deep faking to connect with users by using elaborate personas that can sometimes take months to pull off.
A perfect story of this was the story of a UK energy company that was tricked into wiring $220,000 to a Hungarian company due to an A.I. that could fake a call as the CEO. Thieves are now using AI deepfakes to trick companies into sending them money – The Verge
Deep faking in the cybersecurity context can be a phone call, text, email, or another medium that uses A.I. or extremely engaging social engineering.
A criminal could call someone in accounting after performing deep research on the CEO of that company. That criminal could sound nearly identical to the CEO on the phone, then tell the accountant they will send an email summarizing their conversation. The criminal can then send an email from a spoof of the CEO’s email. The timeliness of these events could trick anyone.
Spear-Phishing

Cybercriminals are realizing that sending broad email attacks that target hundreds of thousands of users is not effective anymore. By nature, broad emails are not personalized and are less easy to nurture into becoming more sophisticated attacks with real dialogue. Phishing emails have historically had a reputation for being cookie-cutter with poor grammar (we’ve all heard of the Nigerian prince email campaign).
Now, with the breadth of user data available for purchase and the amount of personal data users voluntarily publish on sites like Facebook or LinkedIn, cybercriminals are finding tremendous value in spear phishing.
Spear-phishing is the practice of targeting a select few individuals rather than the masses. A spear-phishing campaign can be conducted much like a sales or marketing campaign where the criminals will target certain industries, titles, or demographics.
Example: a cybercriminals syndicate designs ransomware and targets the insurance industry. They will then find employees with potential access access to the network within the company they want to target. They will then conduct research using purchased data, social media, account hacks, etc to spy and make sure they send the right message to the right person. After successfully engaging with someone at a targeted company for a while, incorporating back and forth conversation, the criminals can get that employee to click a malicious link or file, which can then spread the ransomware.
When spear phishing, those that are “low hanging fruit” are often the target. These are those that might have difficulty discerning fake emails. Examples include remote workers, older workers, and those that have minimal exposure to leadership email language.
Case Study
An example of just how convincing a spear-phishing campaign can be is the example of a journalist from India by the name of Nidhi Razdan that thought she was Given a position at Harvard. The campaign targeted her because they found she spoke at a Harvard event in the past by invitation from Harvard. The hackers and journalists corresponded for a long time, even going as far to perform an interview, establish employment terms, and provide a teaching schedule. She only found out it was a scam after she contacted Harvard and they informed her she was never offered the position and the Harvard human resources email she was corresponding with did not exist.
The author has written about her experience and you should read it to learn just how sophisticated phishing campaigns can be.
I Am Nidhi Razdan, Not A Harvard Professor, But… (ndtv.com)
Becoming Extortive

Cybercriminals have changed the purpose of ransomware entirely in some cases. Rather than blocking an organization from its data, the criminals instead extort the organization such as by increasing privileges giving themselves massive control over the business, threatening to release intellectual properties or assets like code. In this way, a business cannot just simply rely on backups. The threat of a data leak compels many to pay the ransom. Especially if they are in an industry that has strict consequences for data leaks like insurance or healthcare.
Extortion dramatically changes how companies implement ransomware protection. Instead of reactive solutions like anti ransomware software or preparing robust backups, your organization must now put prevention at the forefront. In an industry like healthcare, where the data itself is incredibly valuable to extort, an attack cannot breach the prevention systems in place or your company may already have lost. The main concern becomes a data leak rather than if you pay the ransom.
Ransomware as a Service (RaaS)

Ransomware as a service allows cybercriminals to join an established and growing market of ransomware for purchase. The use of this service makes it easier than ever before for criminals with little or no coding knowledge to launch crypto-malware campaigns because they only need the technical skills required to operate web hosting services and distribute spam emails.
There are two notable dangers ransomware as a service creates:
The first is that because ransomware is now available to the masses, criminals with little coding knowledge can now engage in the lucrative market for ransomware attacks. This dramatically increases the chance a business will be attacked. These lesser criminals also may not have the knowledge on how to restore data properly if a ransom is paid. And they are likely performing infrequent or one-off attacks so they don’t have a reputation to protect like established cybercriminal syndicates.
The second danger is that ransomware criminals can now form a community and learn from each other. This allows criminals to become smarter and adapt much faster. And with a greater number of ransomware products on the market, the progress towards more powerful and efficient ransomware becomes far quicker.
How to Respond
Ransomware has changed and so has the playbook for preparing for and responding to a ransomware attack. While much of the same precautions stay unchanged, new solutions have come to market to help organizations better prepare for and respond to attacks.
Understand Your Industry’s Risk to a Ransomware Attack
Certain industries are at a far greater risk of being on the receiving end of a ransomware attack than others. Health data for example has long been prized by criminals because businesses that guard Health data are at risk of severe legal and financial penalties should that data become encrypted, or worse, leaked.
Here are the industries that are the most at risk of a ransomware attack:
- Healthcare
- Legal/Law
- Energy
- Utility
- Education
- Finance
- Government
If your business falls into any of these categories, it is at immediate risk. You should seek immediate ransomware protection and may want to get in touch with a professional cybersecurity auditing firm that can analyze your vulnerabilities.
If your business is not in the above categories, you are still increasingly at risk of being hit with a ransomware attack. You may also be more tempted to pay the ransom if attacked because the ransom may be lower and your business may not suffer the same legal ramifications. Your business should implement most if not all the steps below to minimize your risk of a ransomware attack.
Establish a Response Framework

The NIST framework is a helpful model for organizations to use when establishing their ransomware response plan. NIST has broken down the four steps of handling an incident into specific functions that can be assigned to team members within your organization, ensuring all roles are covered in the event something happens and resources need to be enacted. This ensures that everyone knows what they should do if or when an attack occurs. Involve Key Stakeholders
Here is how the framework works, NIST has defined four primary functions:
- Identify: a business identifies its most important functions, assets, people systems, and capabilities of the organization and establishes tiers of importance so that they know which vulnerabilities to tackle first. This allows a business to focus and become more efficient at covering attack vectors. categories can include things like risk assessment, asset governance, risk management strategy, etc.
- Protect: Create a list of the ways you can protect critical systems from a breach. Categories can include things like training, access control, information protection procedures, etc.
- Detect: create a set of steps to detect if a cybersecurity event occurred. This allows your organization to diagnose whether there is a breach that needs immediate attention. categories can include detection process, anomalies, security monitoring, etc.
- Respond: Develop actions taken in response to an attack. These will help with containing and stopping ransomware. Categories include communication, response planning, mitigation, improvements, etc.
- Recover: Outlines what needs to be done to facilitate a timely recovery and resume normal operations. Categories include recovery steps, communication, systems improvements, etc.
NIST consists of categories and sub-categories:
- Categories: the broad description of what needs to happen. For example, communication. This is an umbrella for more specific communication actions that need to take place.
- Sub-categories: these are the more specific actionable outcomes. For example, in the category “identity management”, you might have a sub-category like. “All employees will use 2FA when logging into organization accounts”.
You can view the specifics of the NIST framework here – the official document covers the framework more in depth. But even just using the basic one sheet framework can help your organization spot an exploit and develop proper planning and response actions. You can also use different or even self-developed frameworks should you feel that there is another that better suits your organization’s needs.
Backups
Modern sophisticated ransomware now targets backup, so the old strategy of using backups to counter an attack may not work. Backups are still important, however. But the backups your organization keeps must be less penetrable. There are 3 tiers of backups your organization should consider.
The first tier is readily available standard backups. These are important because beyond ransomware your organization will likely need to revert changes, so it’s important you have backups that can be modified and easily applied over running systems. These backups include snapshots from your hypervisor or services like Veeam.
The second tier is immutable backups. these are backups that are immutable, or unmodifiable. This means they can be restored to a system but not modified in place on the live OS. These backups should include images of your OS and application installations for short-term recovery point objectives (RPOs). Immutable backups can either be online or offline, with offline offering greater security should you get a network infection.
Why not just keep immutable backups? Because they cannot be modified AT ALL! This means that should your organizations need to make any changes they cannot. So these backups are best kept in case of emergency.
The third tier is air-gap backups. air-gap backup is a backup of a live system that is not connected to any network (or the cloud). An example of an air-gap backup would be tapes physically stored on-premises. They are completely inaccessible from the network or system and therefore unhackable.
Air-gap is important for businesses that deal with sensitive user data where should that data become compromised, there are consequences. Businesses like healthcare for example must also keep data for several years by law. Air-gap offline backups allow healthcare companies to store vast quantities of data securely and cost-effectively.
Implement Regular Training

Regular training is a must these days. Regular training goes a long way because most ransomware attacks occur due to phishing emails, social engineering, RDP exploits, and leaked credentials. Training staff to take care of their credentials, understand good security practices, and treat digital interaction with skepticism will go a long way towards developing your business’ ransomware protection.
Here’s how training could play out at an SMB. When a new staff member is onboarded they receive relatively comprehensive training from IT on what is expected from them regarding security. These can include regular password changes, enabling 2FA, and how to spot malicious emails. IT can then help the employee get set up with an authenticator app, let the employee know password requirements, provide info on device acceptable use. If there is a particular vulnerability that the employee must be made aware of, this can be done during orientation.
Once the employee has had time to settle in their role, they will join the other staff for quarterly training led by IT or other parties that can help with security training. Staff will work in groups and try to identify malicious emails or other forms of communication. For example, letting them listen to a deep fake call and providing the employees a proper response when in doubt.
Employees can then, on their own time once a quarter reset passwords so that systems are harder to hack. The system can be automated to alert employees of password changes and automatically disabling their current password after a certain date.
Establish Policies
Taking guidelines like “urging to change passwords once a quarter” and turning them into requirements like “required to change password once a quarter” can help thwart ransomware. Humans are naturally sloppy when it comes to security because life presents other, immediately visible challenges. However, that doesn’t excuse an organization from not implementing them. Instead, it’s best to have IT or a manager establish policies regarding security. Here are some common ones that can help organizations prevent ransomware.
- requiring frequent password changes
- requiring 2FA to access organization applications
- outlining acceptable use for devices that access organization apps and systems
- recording login/logout
- not using company email to sign up for non-work sites
Implement Zero Trust

One of the most effective forms of ransomware protection is to implement Zero Trust within your organization. Zero Trust is a framework that combines multiple advanced identity management programs to constantly validate users whether inside or outside the organization. For example, your business’ zero-trust policy may require users whether inside or outside the organization to access all apps using a VPN, log in with 2FA, and be a part of an active directory that bestows complete control over user accounts to a high-level systems admin within the organization.
Businesses are increasingly implementing zero trust as one of many forms of ransomware protection.
Zero trust can be difficult to implement for SMBs however because it requires one or a team of competent systems administrators who have the time to actively manage all devices accessing programs and the network. However, if your business can implement zero-trust internally or get help from a third party like an MSP, zero-trust remains an important part of a strong ransomware protection plan.
Invest in Cybersecurity
Virtually all large businesses have a sizable investment in cybersecurity services, systems, and software. And more SMBs are starting to invest a portion of their IT expense directly into cybersecurity.
Cybersecurity is broad and can cover all kinds of services. These commonly include, but are not limited to:
- professional security auditing services
- anti-virus software (Norton, McAffee, Kaspersky, etc)
- ransomware-specific software (Zebra Ransomware Stopper)
- Software/hardware firewalls
- Malware tools (Malware bytes, Bitdefender)
Cyber Insurance

Cyber insurance is not cybersecurity because it plays no role in prevention or recovery, but it provides payment should a business become infected with ransomware. The payment foremost covers liabilities related to ransomware, but can also provide payments to recover data or continue business operations depending on the policy.
Here is an example of a policy from nationwide as an example of what a major insurance company will offer.
Cyber insurance is a newer offering and quickly becoming more expensive as insurance companies see a dramatically increasing number of claims. Most SMBs do not have cyber insurance but it is common now for larger companies that can afford the extra policy.
Consider Linux
Lately, the Windows operating system from Microsoft has been falling out of favor for organizations. Linux in comparison is growing because it is free and open-source (FOSS) and generally doesn’t have the same breadth of vulnerabilities for ransomware and malware to abuse.
Unless your organization runs an application that requires Windows, it should absolutely consider a Linux operating system for running its server or cloud infrastructure. There are many distributions of the Linux operating system to choose from. Common distros prized for stability and security are Debian (used by NASA), CentOS, RedHat Enterprise Linux, and Manjaro.
If employees use a cloud desktop experience (using services like Microsoft 365 or Google Drive) to power their day-to-day operations. A Linux desktop operating system may help tackle security vulnerabilities. However, using Linux is less viable for most organizations than a server setup because the Linux operating system has less support for mainstream applications like Microsoft Office.
Anti-Ransomware Software

If you search for “ransomware protection” or “anti ransomware software” you will likely be bombarded with many competing antivirus programs. A true anti ransomware program solution will not be part of a broader proprietary cybersecurity suite, but will instead seamlessly integrate with your existing solutions.
Zebra Ransomware Stopper is an example of an anti-ransomware software. It is a standalone program, not part of a greater cybersecurity suite, that is focused on rooting out ransomware that has already infected your system. It uses deception technology that deploys honeypot files to attract and trap ransomware, stopping the encryption process from further infecting your machine and network.
Many businesses are actively looking for anti-ransomware software so that they have a plan B in case their preventative measures fail and a system does become infected. If you are a reseller or business looking for a last line of defense consider reaching out to us so we can teach you more about this amazing solution.
You can contact us here to learn more.
Summary
Ransomware is evolving, and because of that, your strategy for preparing and recovering from ransomware needs to change too. Ransomware attacks are increasing in frequency, becoming more sophisticated, turning towards extortion, and using personal information against targets.
The best thing your business can do is to develop a bulletproof strategy that your organization can follow consistently long term. Start with developing a framework then identify services and policies that can help turn that framework into a realistic actionable plan.
To learn more about Zebra Ransomware Stopper and how it can potentially save your business from the long-term consequences of a ransomware attack, you can view our page here.

